LONDON--(BUSINESS WIRE)--Jul 22, 2025--
Intruder, a leader in attack surface management, has launched Autoswagger—a free, open-source tool that scans OpenAPI-documented APIs for broken authorization vulnerabilities. These flaws are still common, even at large enterprises with mature security teams, and are especially dangerous because they can be exploited with little technical skill. Autoswagger is available now on GitHub .
This press release features multimedia. View the full release here: https://www.businesswire.com/news/home/20250722587023/en/
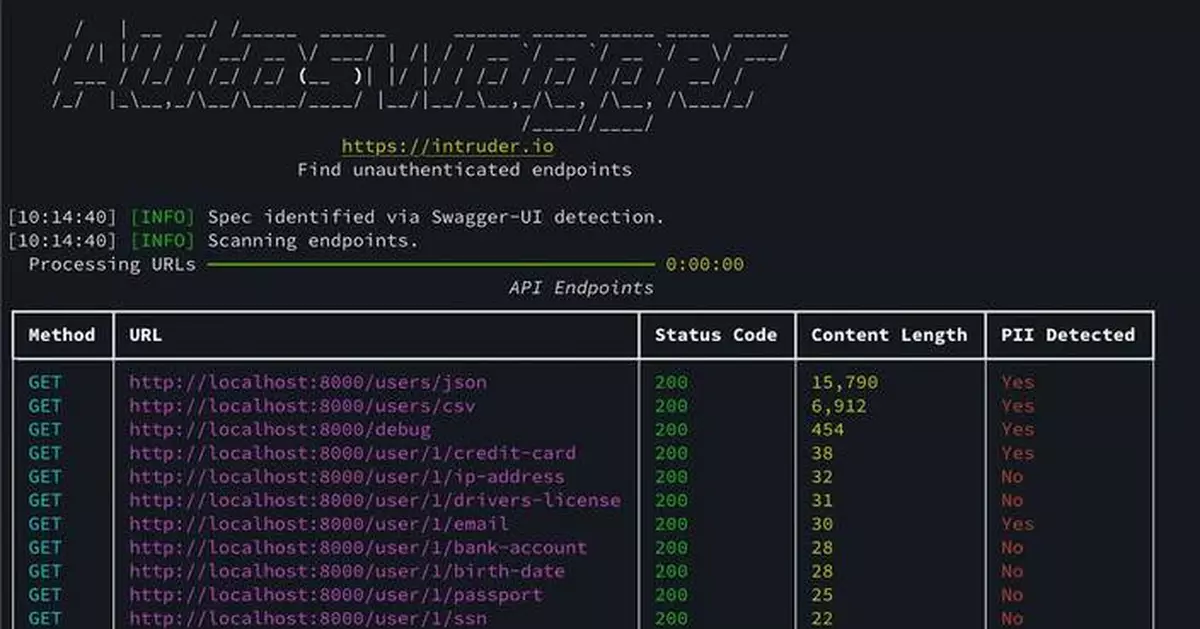
Autoswagger automatically detects authorization weaknesses in APIs and discovers sensitive endpoints not requiring authentication where the application fails to check for a valid API token.
According to Verizon’s 2025 Data Breach Investigations Report, API-related breaches increased nearly 40% year-over-year, with broken authorization cited as one of the most exploited flaws. While there are a wide range of tools that scan APIs, most options to detect broken authorization are either costly, inefficient, or require manual labor from penetration testers to uncover. This is the first freely available tool that is proven effective in detecting these potentially dangerous vulnerabilities.
“These vulnerabilities are so easy to exploit, you could teach someone with no technical background how to do it in a day,” said Chris Wallis, CEO and founder of Intruder. “When you consider how common these issues are and how frequently companies release new code or expose new endpoints, it’s clear this is a critical gap. That’s why we’re making Autoswagger available for free—to help teams find and fix these flaws before attackers do.”
API Sprawl Has Created an Increased Attack Surface for Organizations
APIs have become the backbone of modern applications, and the explosion of APIs has created an increased attack surface for every organization, especially those who depend heavily on third-party APIs (payments, analytics, social login, etc.)—which may introduce risks beyond their control. When broken authorization vulnerabilities are discovered and exploited by bad actors, the results can be very damaging such as the Optus data breach in 2022—when the Australian telecom company ended up paying $140 million AUD in related costs as a result of the sensitive customer data that was extracted via a simple API authorization.
While the attack on Optus brought a lot of initial attention to these vulnerabilities, three years later even members of the S&P 500 still remain exposed. During Intruder’s research and testing of Autoswagger, its security team detected exposed Salesforce records with personally identifiable information (PII) at a large multinational tech company and an exposed internal staff training application that would have allowed potential attackers to run queries against the database at a multinational soda company. Ultimately, this data could have been used to mount a phishing campaign against employees, with real information that could gain the staff member’s trust. The majority of the vulnerabilities discovered during the research process were for APIs intended for internal use.
How Autoswagger Detects Broken Authorization
Autoswagger begins by detecting API schemas across a range of common formats and locations, starting with a list of an organization’s domains. It scans for OpenAPI and Swagger documentation pages, sending requests to each host to locate valid schemas. Once identified, it parses the API specifications and automatically generates a list of endpoints to test, taking into account each endpoint’s definition, required parameters, and expected data types.
From there, Autoswagger executes targeted scans to identify broken authorization flaws by:
For more advanced use cases, Autoswagger can be run with the --brute flag to simulate bypassing validation checks. This helps uncover flaws in endpoints that require specific data formats or values, which may reject generic input.
Finally, the tool analyzes any successful responses for signs of exposed sensitive data, such as PII, credentials or internal records. Any endpoint missing proper authentication and returning sensitive information is included in the output report.
“Exposing documentation for your API effectively increases your attack surface, and as a defence in depth measure, you should not expose API documentation unless it’s a business requirement,” said Dan Andrew, Head of Security at Intruder. “The lesson here is, in addition to regular API scanning after each development iteration, that you shouldn’t publicly document your APIs unless you can’t avoid it. Without a ‘map,’ this kind of vulnerability becomes much harder for attackers to exploit.”
More information about how to deploy Autoswagger and the team’s journey to develop the solution can be found here on Intruder’s company blog. Autoswagger is free to download and install via Github.
About Intruder
Intruder's exposure management platform helps lean security teams stop breaches before they start by proactively discovering attack surface weaknesses. By unifying attack surface management, cloud security, and continuous vulnerability management in one intuitive platform, Intruder makes it easy to stay secure by cutting through the noise and complexity. Founded in 2015 by Chris Wallis, a former ethical hacker turned corporate blue teamer, Intruder is now protecting over 3,000 companies worldwide. Learn more at https://intruder.io.
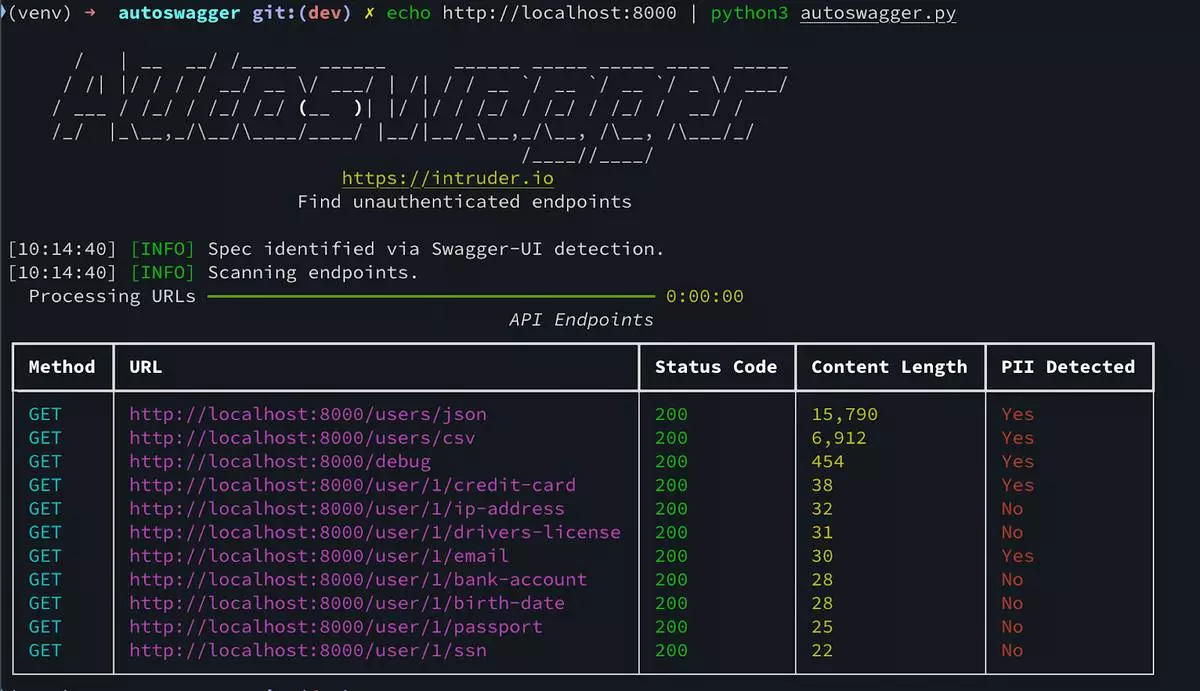

Autoswagger output showing scanned endpoints that are missing authentication, along with an indicator of whether sensitive PII or secrets were discovered in the API response